¶ readme
Things to remember adjust for based on the provided settings from the lab/startup documents.
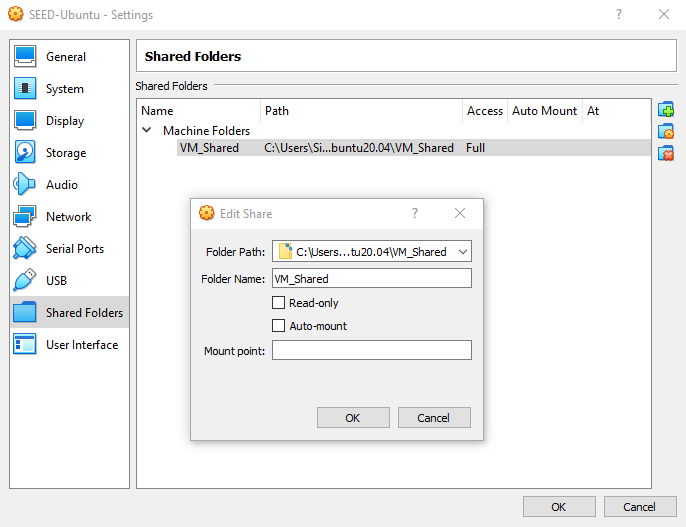
¶ shared folder
- Make sure the machine is completely powered off before changing the shared folder setting (despite the section before this talking about save state)
- Make sure settings for the shared folders has the Auto-Mount option unchecked
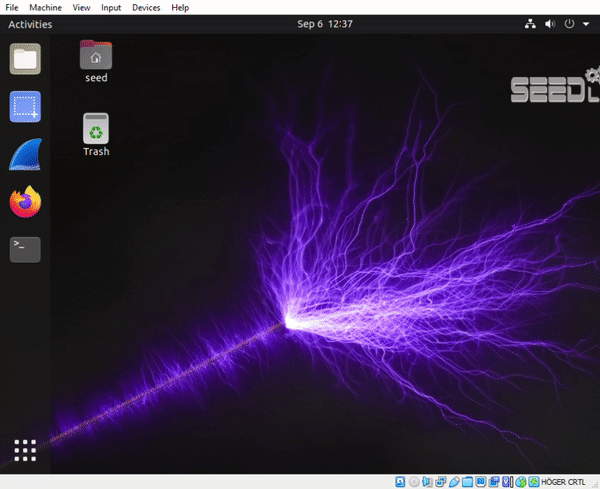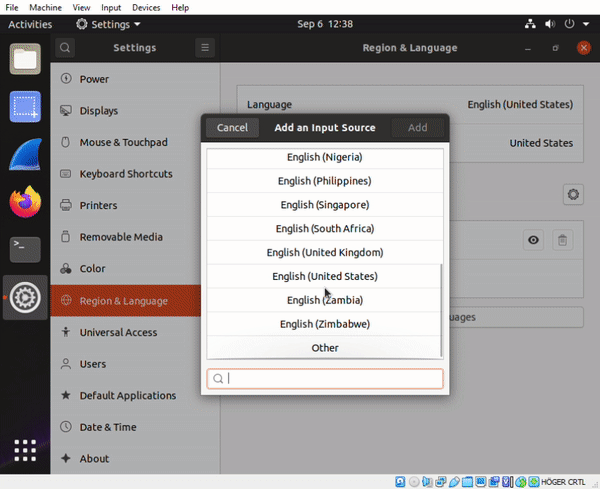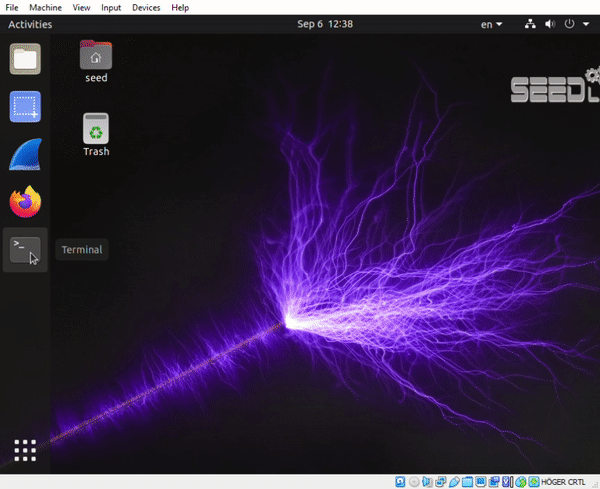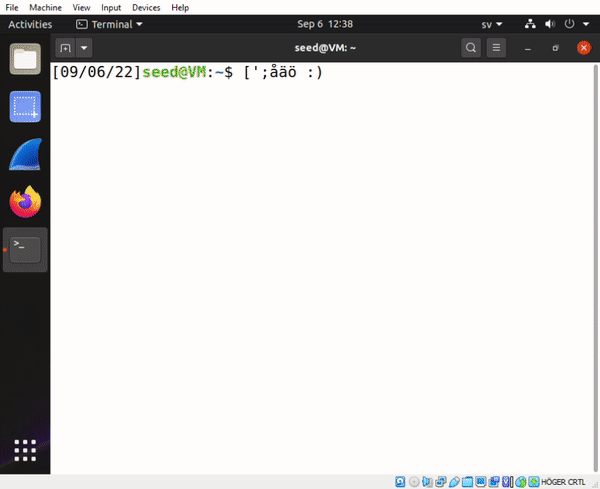
¶ fixing keyboard layout
- If you struggle with english layout for the keyboard, you can adjust it easily in the gui (to match the swedish physical keyboard)
¶ labsetup.zip
Download, extract and then remove the original lab zip
wget -qcO ~/Labsetup.zip --no-check-certificate seedsecuritylabs.org/Labs_20.04/Files/Sniffing_Spoofing/Labsetup.zip && unzip ~/Labsetup.zip && rm ~/Labsetup.zip
When running python files as root (sudo) you need to specify the absolute path (sudo ./filename instead of sudo filename)
¶ docker-compose.yml contents (click copy)
version: "3"
services:
attacker:
image: handsonsecurity/seed-ubuntu:large
container_name: seed-attacker
tty: true
cap_add:
- ALL
privileged: true
volumes:
- ./volumes:/volumes
network_mode: host
hostA:
image: handsonsecurity/seed-ubuntu:large
container_name: hostA-10.9.0.5
tty: true
cap_add:
- ALL
networks:
net-10.9.0.0:
ipv4_address: 10.9.0.5
command: bash -c "
/etc/init.d/openbsd-inetd start &&
tail -f /dev/null
"
hostB:
image: handsonsecurity/seed-ubuntu:large
container_name: hostB-10.9.0.6
tty: true
cap_add:
- ALL
networks:
net-10.9.0.0:
ipv4_address: 10.9.0.6
command: bash -c "
/etc/init.d/openbsd-inetd start &&
tail -f /dev/null
"
networks:
net-10.9.0.0:
name: net-10.9.0.0
ipam:
config:
- subnet: 10.9.0.0/24
¶ python sniffing code interface
#!/usr/bin/env python3
from scapy.all import *
def print_pkt(pkt):
pkt.show()
pkt = sniff(iface='br-XXXX', filter='icmp', prn=print_pkt)
then run: sed "s/XXXX/$(docker network ls | grep net-10.9 | awk {'print $1'})/" sniffing.py -i
The lab instructions says the networks name is seed-net but the network defined in the docker compose file is called 'net-10.9.0.0'
¶ scapy packet sniffing filters
telnet telehack.com to test outgoing telnet
#!/usr/bin/env python3
from scapy.all import *
def print_pkt(pkt):
pkt.show()
#1. filter for only icmp
#pkt = sniff(iface='br-fbd64cad1630', filter='icmp', prn=print_pkt)
#2. filter for tcp from hostB only (10.9.0.6) and destination 23
#pkt = sniff(iface='br-fbd64cad1630', filter='tcp and src host 10.9.0.6 and dst port 23', prn=print_pkt)
#3. filter from or to a subnet. (except a local subnet on the VM - ping to 120.230.0.1)
#pkt = sniff(iface='br-fbd64cad1630', filter='net 128.230.0.0/16', prn=print_pkt)