¶ Mitigate Web Attack (Proxy Based)
End Goal
* set up a bad web-server (example webgoat or DVWA) and perform a “SQL-injection” or “Cross site scripting” → succedd with attack
* Protect the bad web-server with NGFW Fortigate again and perform a “SQL-injection” or “Cross site scripting” → Fail! (now protected)
Read (& Learn) Before the Lab
- https://securingninja.com/dvwa-hacking-tutorial/ "DVWA Hacking Tutorial"
- https://www.sprocketsecurity.com/resources/owasp-top-10-risks-of-2022 "A Showcase of the Top OWASP Risks"
Inspirational Picture:
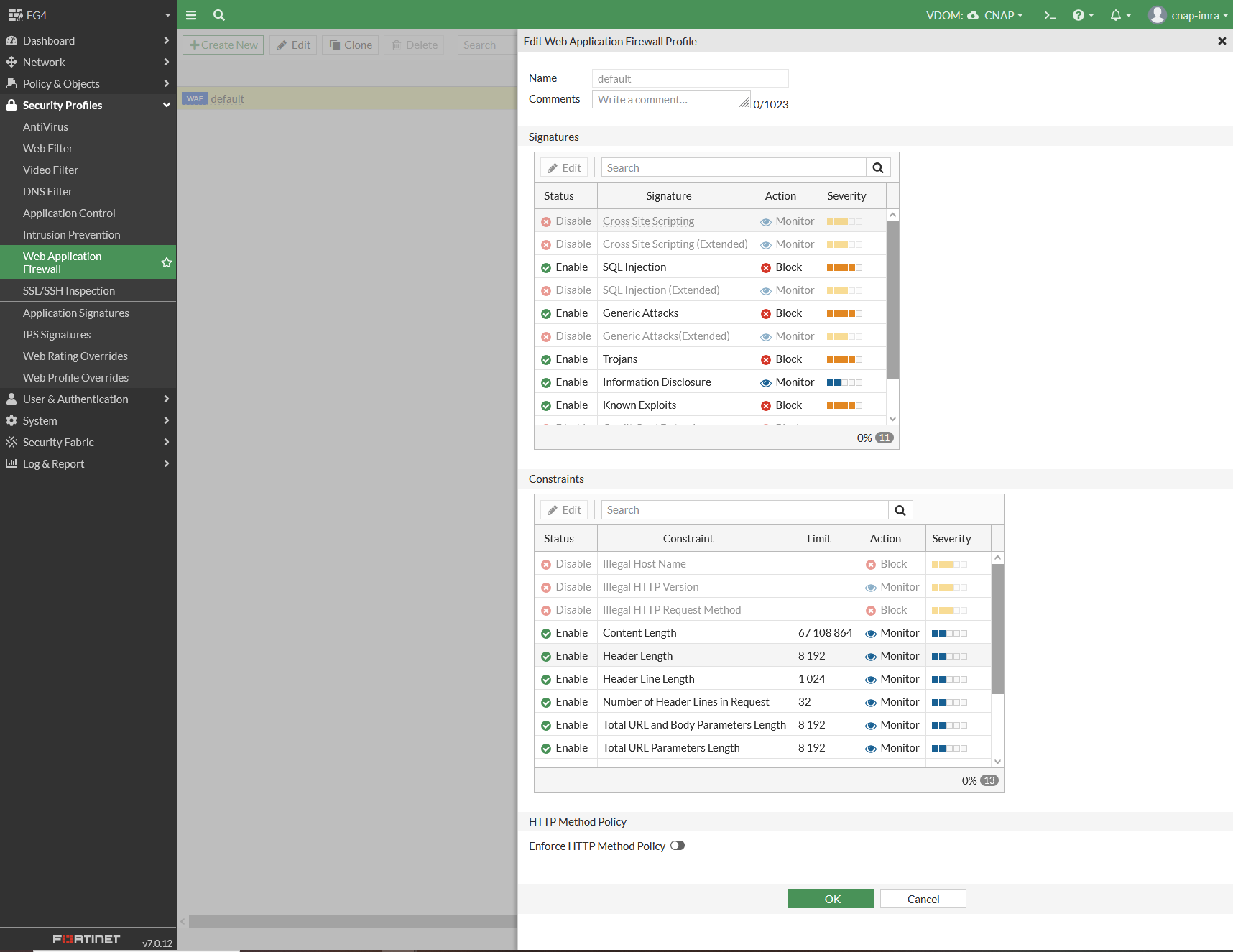
Fortigate Web Application F (WAF) screenshot
Please note “Signatures” and “SQL injection” above
BAD: https://www.youtube.com/watch?v=E4qwpBxH5b4 Web application firewall (WAF) - firewall training
Good: https://www.youtube.com/watch?v=TYdzj1XMMAI
¶ 1. Topology
Below is a picture of the NG-firewall that you will use. Please go and find it in your POD. It is forbidden to use NGFS's from other POD's.

Cable according to the below topology
- Connect Kali-PC to Fortigate-Port1 via wall
- Connect Fortigate WAN-port to "Internet"-switch (rightmost ports)
- Connect Windows-PC to "Internet"-switch (rightmost ports) via wall
¶ 2. Test connectivity
- On Windows-PC: test the web browser for Internet-connectivity
- On Kali-PC: type
ip ato find out what XX is in the 192.168.1.XX address of eth0-interface - On Kali-PC: test the web browser for Internet-connectivity
¶ 3. Install DVWA into Kali Linux
Install DamnVulnerableWebApplication (dvwa) into Kali-Linux
-
sudo apt-get update
-
sudo apt-get install dvwa
-
sudo dvwa-start
-
surf to 127.0.0.1:42001
FIX ACCESS RULES WITH:
sudo dvwa-stop
sudo nano /etc/dvwa/vhost/dvwa-nginx.conf
change two occurrences of “deny all” to “allow all”
sudo dvwa-start
- surf to 192.168.1.XX:42001
¶ 4. Fortigate - Initial Setup
This is the actual lab: previous things where only initial setup/prerequisites
Do not do the inital setup; press Later , Disable , Don't or Optimal .
- Use Kali Linux & Firefox to surf to https://192.168.1.99 (or whatever Linux command ip route ↲ (Windows: ipconfig /all ↲) tells you that the default gateway is)
- Login with username admin and blank password
- Change password to Network!337 (Previously: F0rt!.hv.gov or 2001:6b0:: )
- Change the hostname to forti-pod-X where X is the pod the NGFW is in (look at the top of the rack)
- Do * not * upgrade the Fortigate; only version 7.4.9 works with this lab (in 2023 it was 40F with 7.3.6 due to 2GB restrictions )
- Go to ↕️↔️ Network > Interfaces. Locate WAN interface and write down the address (should be 192.168.16.xx)
¶ 5. Fortigate - Port Forward
https://getlabsdone.com/how-to-configure-fortigate-port-forwarding/
The topology is as depicted in the diagram below:
NAT works very well for the "inside" kali-PC to access the Internet, but no one on the "outside" (Internet) can reach the kali-PC. TCP session are only one way.
Lets fix it with Port Forwarding that lends a TCP port on the fortigate, and routes that traffic to the Inside.
- Go to 📄Policy & Objects > Services: Create New Service "dvwa-42001-service" //Category: WebAccess // DestinationPort:TCP:42001 42001
- Go to 📄Policy & Objects > Protocol Options: Clone "default" and create "robert-default"
Edit "robert-default" Edit "robert-default: and change http "80" to "80,8080,42001"
Blog-NonStandardPortInspection - Go to 📄Policy & Objects > Virtual IP: Create New VIP "dvwa-vip" // External:192.168.16.__ // MapTo: 192.168.1.__ Enable PortForwarding: Tcp: OneToOne: 42001,42001
- Combine these three with some more data, and create a Policy:
Go to 📄Policy & Objects > Firewall Policy: Create New Policy "allow-dvwa-policy" that uses "dvwa-service" and "dvwa-vip"
Remember that dvwa uses port# 42001 for http traffic, not 80
55 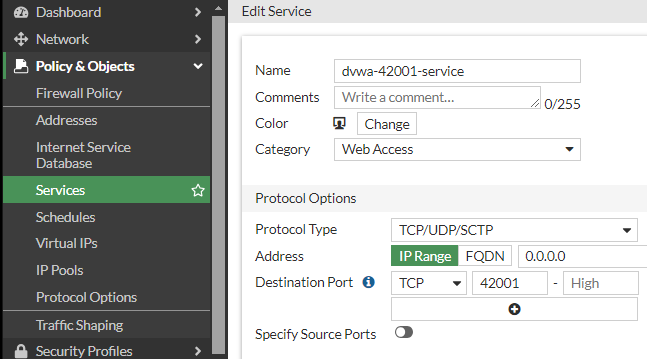 +
+
56 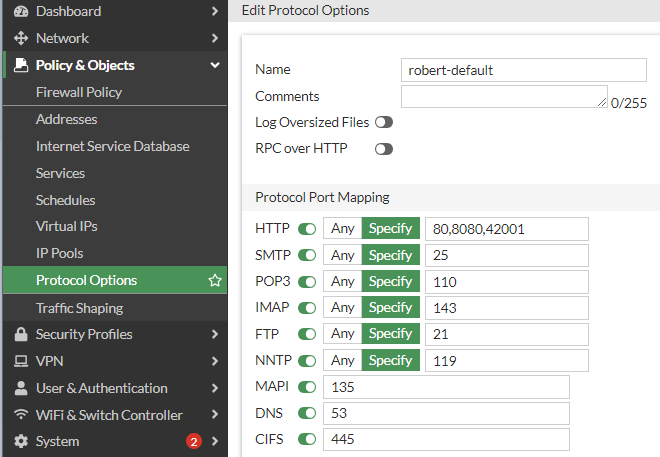 +
+
57 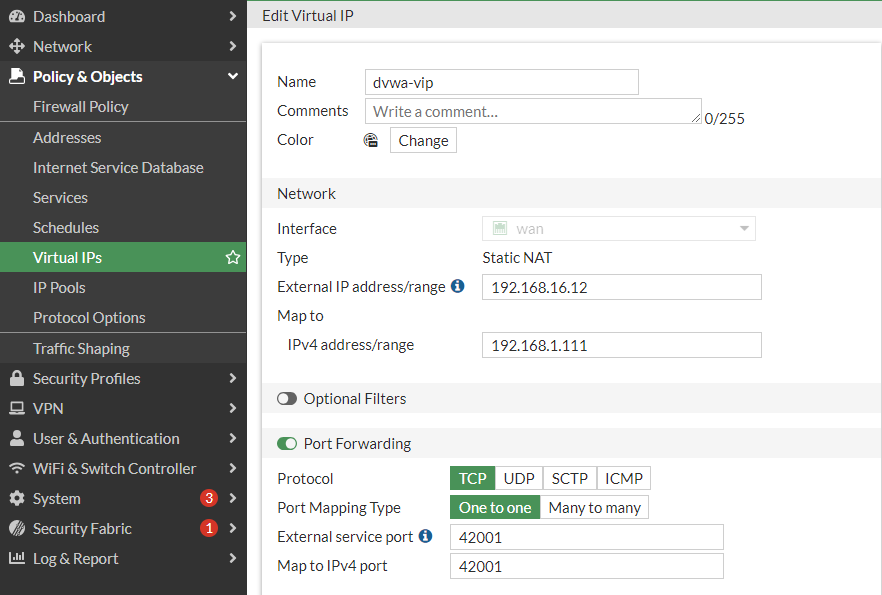 +
+
⬇️
58 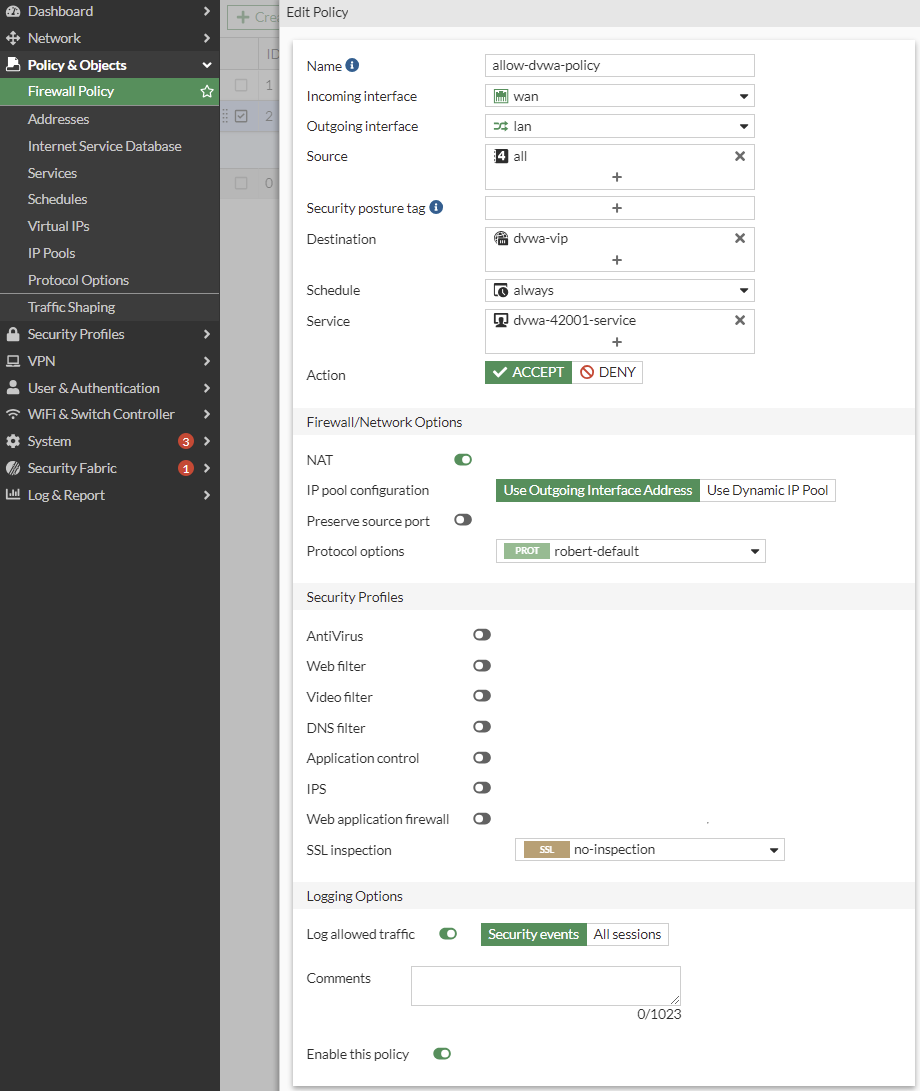
⬇️
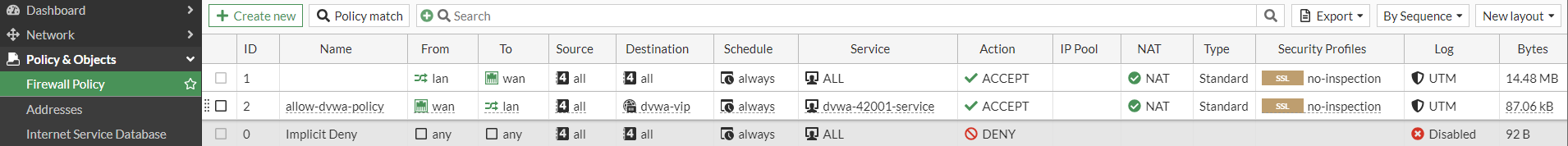
¶ 6. Attack DVWA (Attack Successful)
-
Access DVWA from the outside Windows PC with http (not https) using the URL http://192.168.16.XX:42001
-
Troubleshoot Port-Forward NAT if you can not see the http web-page
-
Go to DVWA Security: Change Security Level to "low"
CROSS SITE SCRIPTING (XSS) ATTACK -
Go to XSS (reflected) and enter Robert
-
Go to XSS (reflected) and enter <Script>alert("hacked by Robert")</Script>
Read more: https://tanmay26.medium.com/cross-site-scripting-xss-dvwa-damn-vulnerable-web-applications-36808bff37b3
SQL INJECTION ATTACK -
Got to Setup/Reset DB: Click button "Create/Reset Database"
-
Go to SQL injection and enter 1
-
Go to SQL injection and enter %' or '1' = '1 Beware of the difference of ', ` and ´ characters :- )
Read more: https://medium.com/@tafiaalifianty/low-level-sql-injection-in-dvwa-41928b7206c6
¶ 7. Fortigate - Web Application Firewall
Manual: FortiGate / FortiOS 7.4.1 Administration Guide Protecting a server running web applications
Picture
- Click ⚙️System > Feature Visibility, and turn on Web Application Firewall. Click Apply
- Features must first be enabled via CLI first:
set proxy-and-explicit-proxy enable
end
config system settings
set gui-proxy-inspection enable
end
Click top right corner >_ symbol for CLI
- Click 🔒Security Profiles > Web Application Firewall
- Create an empty profile by clicking [+ Create New], naming it “waf-profile2”,
Enable both Cross Site Scripting and set action to BLOCK
Enable both SQL Injection and set action to BLOCK - Go back to "📄Policy & Objects > Firewall Policy" and edit your NAT Policy
- Change "Inspection Mode" to "Proxy-based" (from "Flow Based")
- Enable "Web Application Firewall"
- Change WAF to "waf-profile2" (your previously created WAF, not the default one)
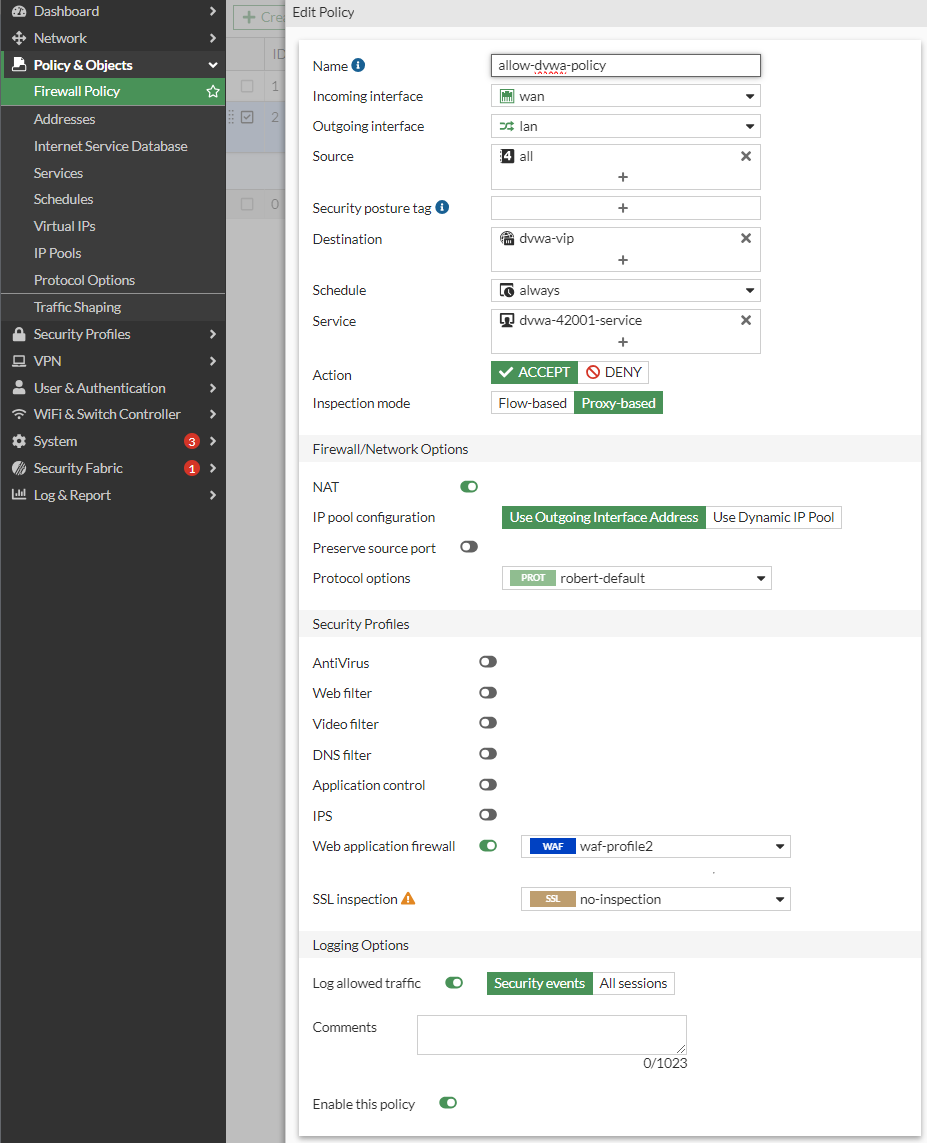
¶ 8. Attack DVWA (Attack Mitigated)
-
Access DVWA from the outside Windows PC with http (not https) using the URL http://192.168.16.XX:42001
-
Troubleshoot Port-Forward NAT if you can not see the http web-page
-
Go to DVWA Security: Change Security Level to "low"
CROSS SITE SCRIPTING (XSS) ATTACK -
Go to XSS (reflected) and enter Robert
-
Go to XSS (reflected) and enter <Script>alert("hacked by Robert")</Script>
Read more: https://tanmay26.medium.com/cross-site-scripting-xss-dvwa-damn-vulnerable-web-applications-36808bff37b3
SQL INJECTION ATTACK
5.1 Got to Setup/Reset DB: Click button "Create/Reset Database"
5.2 Go to SQL injection and enter 1
5.3 Go to SQL injection and enter %' or '1' = '1 Beware of the difference of ', ` and ´ characters :- )
Read more: https://medium.com/@tafiaalifianty/low-level-sql-injection-in-dvwa-41928b7206c6

¶ 9a. Questions
x0. Include a screenshot of the blocked attack, you must include the full screen (with the date/clock in the bottom right corner)
Optional: Last update of WAF signature file? Frequency of updates? Number of signatures in WAF signature file?
x1. What is an ASIC compared to a CPU?
x2. What kind of ASICs (processors) does Fortinet produce? (different ones for different products)
x2b. whic one is used in Fortigate 50G?
HARDWARE
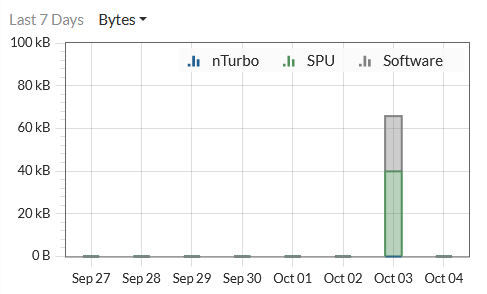
x3. In the above picture (open/edit a policy in Policy&Objects > FirewallPolicy) you see nTurbo, SPU and Software. Explain these three!
x4. Find a (scientific) article that measures SNORT on regular (off the shelf) CPU, or similar measurments.
x4a. What is the title of the article?
x4b. Summarize the findings in 2-3 sentences!
¶ 9b. What about SSL-traffic and https:// ?
Do only one of the following alternatives (XOR)
Alternative 1 - Preferred (hard)
Alt1: Submit a short how-to guide how you succeeded in mitigating a SQLi attack over a https connection (including screenshots)
Alternative 2 - Please don't (easy)
Alt2a: Can you get a free signed https certificate on the Internet? If so, where?
Alt2b: Explain with a figure and text what a Man-in-the-Middle (MitM) is!
Alt2c: Explain what a web server proxy is and how it can function with todays use of https
¶ 10. Cleanup
Erase the Fortigate, so it is clean for the next group, by pressing the >_ icon (top right corner)
Type: execute factoryreset
¶ Youtube
https://www.youtube.com/watch?v=E4qwpBxH5b4 Web application firewall (WAF) - firewall training (forti Tip)
https://youtu.be/Kn27rdcn7tk?si=tEP2QFdI28eB3p2l FortiGate WAF David Romero Trejo (No talking, music only)
https://community.fortinet.com/t5/FortiGate/Technical-Tip-How-to-collect-Web-application-firewall-WAF/ta-p/274390
https://community.fortinet.com/t5/FortiGate/Troubleshooting-Tip-How-to-investigate-if-WAF-is-not-generating/ta-p/196635