¶ Become Vulnerable
- RELOAD PAGE from time to time
- [previously] “ Lab 1 - Introduction to the Internet and the OSI-model ” Addressing, Addresses,
- [previously] “ Lab 2 - Reconnaissance Phase "
- [previously] “ Lab 3 - Vulnerability Scan ”- Use OpenVAS and Nessus to scan for vulnerabilities in the networks found in Lab 2.
- [now] “ Lab 4 - Become Vulnerable, Be the Target " - Now we flip the situation, we passively sit and wait to be attacked, exposed to all the dangers of the (nowadays evil) Internet.
¶ Become Vulnerable

By putting a computer on the Internet, unprotected and without any type of firewall, what (malicious) traffic will it attract?
¶ TASK1: Are there incoming (TCP) packets that we did *NOT* ask for?
First you gather a lot of data for a long time, then you save the data into a file, and finally you present the data in three different ways in SPLUNK.
¶ Subtask 1a: Collect Data
- Start Kali Linux
- Make sure that you have a public IP-address by connecting your Kali-computer to port 1 through 12 and check with ifconfig command
- The firewall ‘iptables’ is already installed, do nothing
- Check the firewall rules with iptables -v -L and note that the chain INPUT is empty (and default policy is ACCEPT)
- QUESTION 1: What is TCP SYN packet? When & why does they occur? What does that have to do with separate “Sessions” (aka “Flows”)?
- Add a logging rule of all TCP SYN-packets, and save to a file
iptables -A INPUT -p tcp --syn -j LOG --log-prefix="robert "
or, even better,
iptables -A INPUT -m state --state NEW -j LOG --log-prefix="robert "
- QUESTION 2: What new do you learn from the interactive page https://explainshell.com/explain?cmd=iptables+-A+INPUT+-p+tcp+--syn+-j+LOG
- Verify with above check-command of the rule. “Packets" and “bytes” should now increase
Check that the log file is growing by the minute with the command journalctl | grep robert
EXAMPLE
Aug 4 13:23:00 kali kernel: robert IN=eth0 OUT= MAC=a2:be:d2:ab:11:af:e2:f2:00:00 SRC=192.168.2.115 DST=192.168.1.23 LEN=52 TOS=0x00 PREC=0x00
TTL=127 ID=9434 DF PROTO=TCP SPT=58428 DPT=443 WINDOW=8192 RES=0x00 SYN URGP=0
¶
Subtask 1b: Create a Datafile from iptables-logs
QUESTION 3: Collect iptables-data for 4 hours. How many attacks per minute? Generate the below histogram with logarithm(10) y-axis of most attacked ports! List the 10 least attacked ports
You can use excel (bad), or learn how to use SPLUNK below (good)
TIP: Use the command journalctl | grep robert > attacker.log to create a file with only your data
¶ TASK 2: SPLUNK - Installation and Visualization of raw data

SPLUNK is a commercial alternative to ELK-stack i.e. Elasticsearch, Logstash & Kibana
- Watch the youtube video: anything that explains SPLUNK & (TCP) Port-numbers
¶ subtask 2a: install the software SPLUNK
- Download binary “SPLUNK Enterprice” or use the
* cloud demo “Splunk Cloud Platform” from https://www.splunk.com/en_us/download.html
* windows installer:curl -v -v --output splunk.msi "https://download.splunk.com/products/splunk/releases/10.0.1/windows/splunk-10.0.1-c486717c322b-windows-x64.msi"
* linux installer:wget -O splunk-10.0.1-c486717c322b-linux-amd64.deb "https://download.splunk.com/products/splunk/releases/10.0.1/linux/splunk-10.0.1-c486717c322b-linux-amd64.deb" - Install and make sure you use the secure(?) password Network!337 (exclamation mark, not 1)
- Import data into splunk
Not so difficult
¶ Subtask 2b: Create Lin-Log diagram in SPLUNK
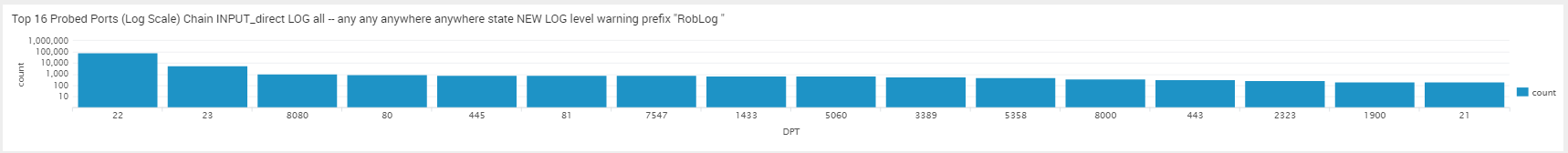
^^^ Look! the number do not go in equal steps (linear) like 10,20,30,40,… the multiply by 10 (log10) 10, 100, 1000, …. Now you can see small (5) and big (1 000) in the same graph, as well as Zero (0)
¶ Subtask 2c: Draw a map in SPLUNK
Search data and Draw the Map
- Click on the large green button "Search & reporting"
- View all your data in "excel" format
source="/var/log/attacker.log"
- Select SRC data by typing SRC ( or | SRC )
source="/var/log/attacker.log" SRC
- Pipe SRC-data into stats-module: source="/var/log/attacker.log" SRC | stats count by SRC
0.0.0.0 123
1.0.232.123 23
1.1.12.4 12
- SRC | stats count by SRC | iplocation SRC
SRC count City Country Region lat lon
0.0.0.0 176
1.0.243.134 1 Thailand 13.75000 100.46670
123.10.169.5 1 Uddevalla Sweden 58.34980 11.93560
1.10.170.79 1 Thailand 13.75000 100.46670
1.11.242.151 1 Seoul Rep. of Korea Seoul 37.51110 126.97430
- Plot data with geostats:
SRC | stats count by SRC | iplocation SRC | geostats latfield=lat longfield=lon count
TIP: you might need to click the tab /Visualzation\ and select Cluster Map
NICE MAP
latitude Longitude Count
-49.12312 -68.123123 12
12.45234 31.1231 7
-12.12312 12.1233 300
- Save the map to your dashboard by clicking "Save As "
¶ SubTask 2d: List the 16 Worst towns in Sweden
SRC | iplocation SRC | search Country="Sweden" | stats count by City | sort - count | head 16
- Click "Save as "
¶ SubTask 2c: Summarize all your result in a DASHBOARD
Final Result of three (3) on a dashboard:

QUESTION 4 Generate the above dashboard with three ELEMENTS (1. Lin-Log histogram of ports attacked, 2. Map of source locations, 3. top Swedish towns that attacked your computer) and put a screenshot of it in your report
¶ TASK3: That was boooring!
QUESTION 5 Explain why Robert thinks the above is boring?
Hint1: In programming syntax is boring & semantics are less boring Hint2: Filter traffic on port# is boring (see screenshot above), but filter traffic with _____ actually makes sense in today's threat landscape.
QUESTION 6 Explain:
a/ DPI
b/ NGFW
QUESTION 7 Can the above be solved with a firewall from the 80'-ies, or do you need cyberwall (also called NGFW) with Deep Packet Inspection (DPI) etc? Motivate!
QUESTION 8 What kind of traffic pattern (port usage) will data-traffic have in a modern environment with Google Document, taxdepartment.gov.se and other internet services. From what sources will traffic come from?
¶ TASK 4: Install a honeypot (T-POT 🍯)
Intro
Firstly: The idea behind T-Pot🍯 is to create a system, whose entire TCP network range as well as some important UDP services act as honeypot.
Secondly: to forward all incoming attack traffic to the best suited honeypot daemons in order to respond and process it.
Warning!
* You must first install Ubuntu Linux, then install t-pot into Ubuntu
Watch Youtube
- Telekom t-pot https://github.security.telekom.com/2022/04/honeypot-tpot-22.04-released.html
- https://www.youtube.com/watch?v=fq5TJd97EeM
- Tpot cowry https://m.youtube.com/
- Threat hunting with T-POT https://www.youtube.com/watch?v=_979DllNLtU
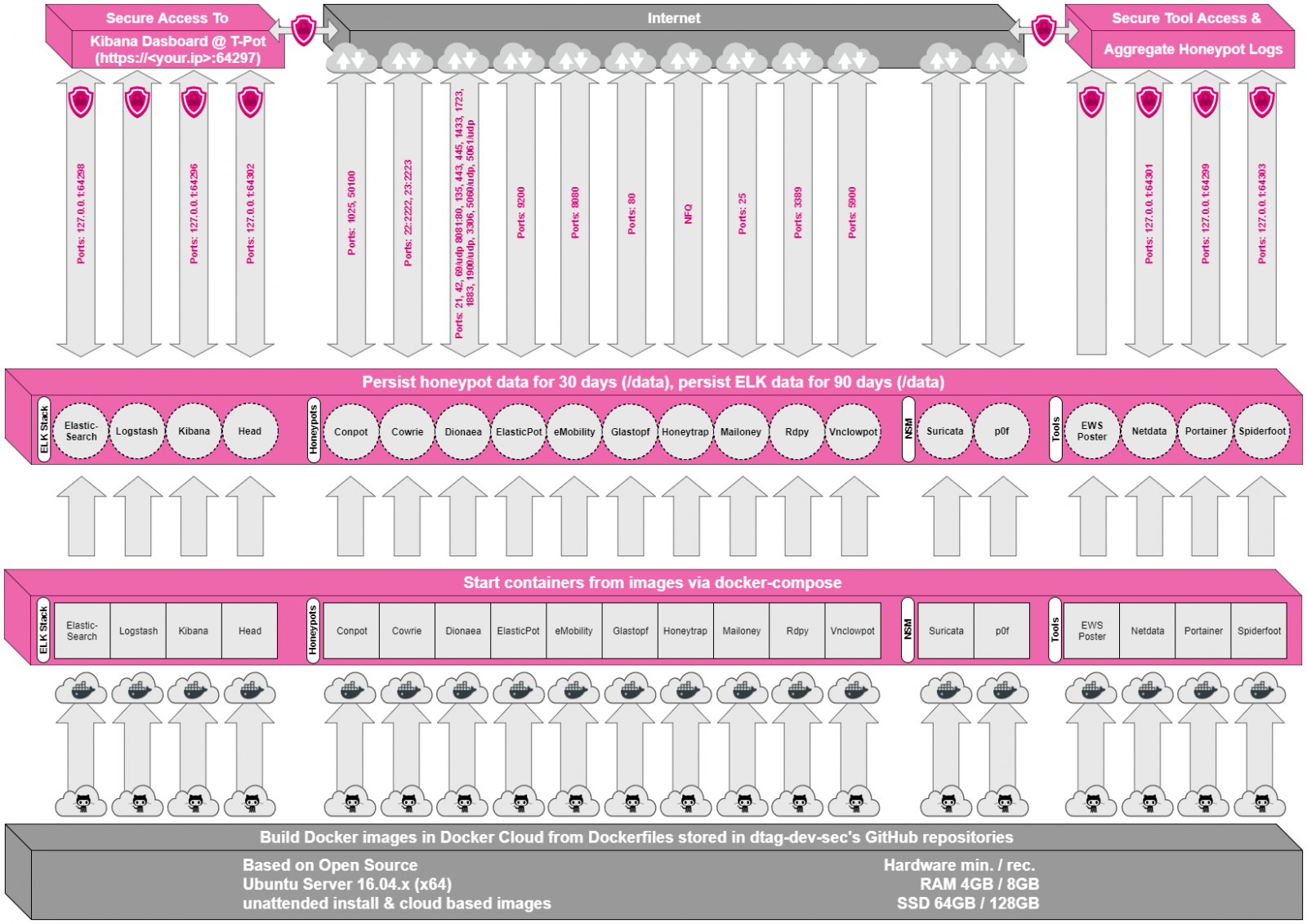
QUESTION 9 What is a container (not a Virtual Machine) and what is it used for?
QUESTION 10
a/ Explain the above architecture of T-Pot!
b/ According to your port-histogram in SPLUNK, what subsystem container honeypots will be mostly used?
¶ :🐧: Install Ubuntu-server to Harddisk :🐧: on a computers HD
- Connect a computer from the wagon to a display, keyboard and to the network
- Find a blue, not black, USB-port and connect the black USB-key
- Boot from black USB-key by rebooting and rapidly pressing <F12> to enter “one time boot menu” (USB contains Ubuntu server)
- Select "UEFI: Kingston …" or whatever to boot from the USB-stick
- Install Ubuntu (no proxy server)
- Select “cisco” for all names, and use the password Network!337
- Skip “Pro”,
- Install SSH-server.
- Skip all packages
- Reboot when done
¶ :🍯: Installation of T-Pot🍯
- as non-root: Clone the GitHub repository: $
git clone https://github.com/telekom-security/tpotce - cd tpotce
- ./install.sh
- Type: (H)ive == T-pot Standard
- Always username cisco password Network!337
- After installation completes: shutdown -r now to reboot
- login again and check your IP with ip a | grep 19
¶
Management of T-Pot🍯 on a computers HD
- Go (walk) to another computer (connected to Private IP address, VLAN 16)
- Browse to the page https://192.168.16.XX:64297 where XX is your T-Pot🍯 servers IP#
Now you can remotely manage your honeypot-server-installation over the web - Login, and select Kibana
- Select T-Pot and see an overall picture of your system
- Go back to Kibana's main menu, and choose your favorite honeypot (like Cowrie or Suricata or …) and make sure you see incoming packets (or events)
¶ Physically move the server to a safe place
- Gracefully shutdown your server
- Remove all cables
- Put it on the floor in Rack-C
- Only connect 2 cables: Power and Ethernet (to Virus-port)
- Temporarily use a monitor to see the new IP-address of the T-Pot🍯 server
- Walk back to your normal computer and connect it to a public IP (CNAP-Switch, port 1 through 12) and surf to
https://193.10.203.XX:64297 where XX is the T-Pot🍯 servers IP#
¶ Questions
QUESTION 11 Read the documentation for https://suricata.io/ and Cowrie ReadTheDocs // XYZ. Evaluate the difference between Cowrie and Suricata; Why choose one over the other; what are your findings?
QUESTION 12 From the table below;
a/ which of the 4 attacks ("Cross site scripting", "SQL Injection", "Trojans" & “Information Disclosure”) can you observe in T-Pot🍯?
b/ How many of each?
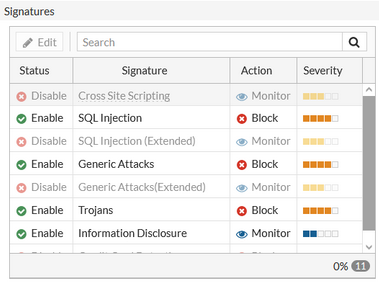
QUESTION 13 From the table above and the figure “T-Pot🍯 Architecture” above; which honeypot is most suitable for finding this type of attacks?
QUESTION 14 Make sure that you have at least 24 hours of data in T-Pot🍯
a/ Change the time interval (top-right) to last 24 hours/one day
b/ What CVE (attack) do think is the most serious that your vulnerable system has been attacked with (Probably not the one with the highest CVSS score)
c/ Make a screenshot of the most interesting (or funny) thing you have discovered in the T-Pot🍯 arsenal of honeypots. Motivate!
QUESTION 15 I Think the ASA-honeypot is the most obscure & niche honeypot in the T-pot🍯 collection
a/ Find another honeypot that you find as obscure & niche as possible!
b/ Are there any attacks against that honeypot?
QUESTION 16 Assume that your Computer Systems for honeypots have a cool graphics-card (GPU) that works well with AI-tasks
a/ Name som AI based honeypots
b/ What use are they (AI honeypots) that differ from the other ~10 classical honeypots in T-Pot🍯 , and what kind of traffic do they attract?
vvvvv OLD STUFF vvvvv PLEASE IGNORE vvvvv
- under Roberts Courses // INT202
¶ Old text Redhat only, *not* KALI/Ubuntu: (Install SPLUNK)
- install splunk do NOT install splunk if you alreade have installed it
wget -O splunk-6.5.3-36937ad027d4-linux-2.6-x86_64.rpm 'https://www.splunk.com/bin/splunk/DownloadActivityServlet?architecture=x86_64&platform=linux&version=6.5.3&product=splunk&filename=splunk-6.5.3-36937ad027d4-linux-2.6-x86_64.rpm&wget=true'
echo "--------------------------"
yum localinstall splunk-6.5.3-36937ad027d4-linux-2.6-x86_64.rpm
rpm -ql splunk | grep splunk
$ echo "--------------------------"
# firewall-cmd --add-rich-rule='rule family="ipv4" port port="8000" protocol="tcp" accept'
¶ 2022 Installation of T-Pot🍯 on a computers HD
- OLD 2022 Do NOT boot this on your personal computer, it will be killed and reformatted
- Connect the target-PC to the internet before you start installation (private address VLAN 16)
- Press F12 to change to 1/ Legacy boot 2/ then boot from the USB-stick
- Answer Swedish (.se) to all Language/locale/… questions
- Use the Password Network!337 (the one is an exclamation mark)
- if prompted; use the username cisco
- Installation is finished when prompted with
WEB: https://192.168.16.XX:64297
ADMIN: https://192.168.16.XX:64294
^BLACKHOLE: [ DISABLED ]
InterimUnit Login: _ - Do Not login! walk away
¶ Robert is troubleshooting T-Pot🍯
| Port | Protocol | Direction | Description |
|---|---|---|---|
| 80, 443 | tcp | outgoing | T-Pot Management: Install, Updates, Logs (i.e. OS, GitHub, DockerHub, Sicherheitstacho, etc. |
| 64294 | tcp | incoming | T-Pot Management: Sensor data transmission to hive (through NGINX reverse proxy) to 127.0.0.1:64305 |
| 64295 | tcp | incoming | T-Pot Management: Access to SSH |
| 64297 | tcp | incoming | T-Pot Management Access to NGINX reverse proxy |
| 5555 | tcp | incoming | Honeypot: ADBHoney |
| 5000 | udp | incoming | Honeypot: CiscoASA |
| 8443 | tcp | incoming | Honeypot: CiscoASA |
| 443 | tcp | incoming | Honeypot: CitrixHoneypot |
| 80, 102, 502, 1025, 2404, 10001, 44818, 47808, 50100 | tcp | incoming | Honeypot: Conpot |
| 161, 623 | udp | incoming | Honeypot: Conpot |
| 22, 23 | tcp | incoming | Honeypot: Cowrie |
| 19, 53, 123, 1900 | udp | incoming | Honeypot: Ddospot |
| 11112 | tcp | incoming | Honeypot: Dicompot |
| 21, 42, 135, 443, 445, 1433, 1723, 1883, 3306, 8081 | tcp | incoming | Honeypot: Dionaea |
| 69 | udp | incoming | Honeypot: Dionaea |
| 9200 | tcp | incoming | Honeypot: Elasticpot |
| 22 | tcp | incoming | Honeypot: Endlessh |
| 21, 22, 23, 25, 80, 110, 143, 443, 993, 995, 1080, 5432, 5900 | tcp | incoming | Honeypot: Heralding |
| 21, 22, 23, 25, 80, 110, 143, 389, 443, 445, 631, 1080, 1433, 1521, 3306, 3389, 5060, 5432, 5900, 6379, 6667, 8080, 9100, 9200, 11211 | tcp | incoming | Honeypot: qHoneypots |
| 53, 123, 161, 5060 | udp | incoming | Honeypot: qHoneypots |
| 631 | tcp | incoming | Honeypot: IPPHoney |
| 80, 443, 8080, 9200, 25565 | tcp | incoming | Honeypot: Log4Pot |
| 25 | tcp | incoming | Honeypot: Mailoney |
| 2575 | tcp | incoming | Honeypot: Medpot |
| 6379 | tcp | incoming | Honeypot: Redishoneypot |
| 5060 | tcp/udp | incoming | Honeypot: SentryPeer |
| 80 | tcp | incoming | Honeypot: Snare (Tanner) |
| 8090 | tcp | incoming | Honeypot: Wordpot |